Set up Portal SSO
ENVIRONMENT: Datto Partner Portal
This article discusses how to set up SSO for the Datto Partner Portal.
Portal SSO lets users authenticate in the Datto Portal by using their existing IDP for single sign-on (SSO) over OIDC protocol. With this feature’s release, you can manage user access for Datto the same way you manage other apps used company-wide for a secure, consistent user login experience.
Prerequisites
Before setting up this feature:
- You must have a Datto Partner Portal user account for your organization.
- You must designate a user as a Security Admin. Only the Security Admin will be able to configure Portal SSO on the Security Settings page in the Datto Partner Portal when Portal SSO becomes generally available.
- The IDP and Datto Portal user accounts, especially the email accounts, must be in sync with each other for each user.
Key considerations
- Organization users can only use SSO if they use the same IDP as the Employee.
- Users with multipartner accounts cannot use SSO at this time. They can continue using the default Datto (AuthWeb) login process.
- When Portal SSO is enabled, Datto Portal IP Management and Portal Login Email Alerts will be disabled, as all authentication security including MFA, IP management, and alerts should be handled by the IDP.
- When Portal SSO is enabled, Authy MFA configurations, under the Security Settings page in Datto, will be reset and disabled. Later, when you remove Portal SSO configuration, you must configure MFA again on the Security Settings page.
- When Portal SSO is enabled the system will disregard Datto user passwords and the Change Password feature will not be effective.
- Datto has verified the following IDPs for use with Portal SSO: Microsoft Entra ID, Okta, and Ping.
- When Portal SSO is configured for Employee Only, users with both Employee and Organization accounts will be unable to use SSO and must log in through Authweb.
- Portal users who have not set up MFA within seven days of account creation will be automatically deactivated. A Portal Admin can reactivate the account and assist with MFA setup to enable Portal login.
How to...
Setup procedure
NOTE You must have the role of Security Admin to complete the Portal SSO setup process.
1. In the Datto Partner Portal, click Admin, then select Security Settings from the drop-down menu.
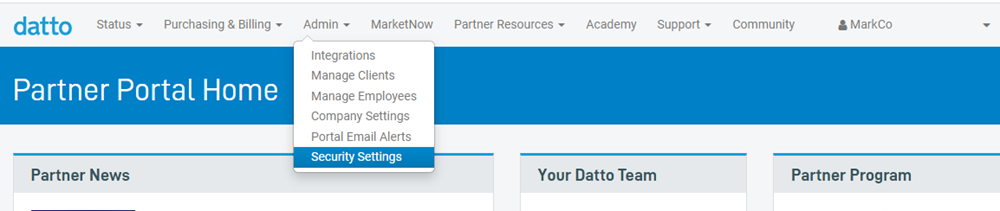
Figure 1: The Datto Partner Portal
2. On the Security Settings page, scroll down to the Single Sign-on (SSO) card and click SETUP OIDC SINGLE SIGN-ON (SSO).
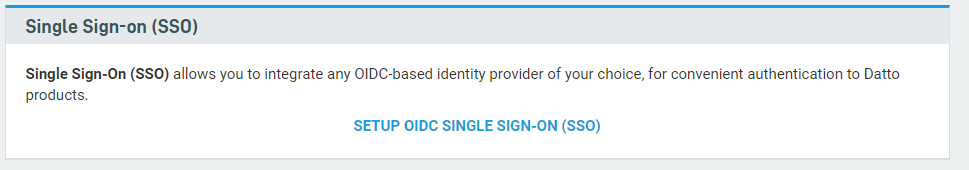
Figure 2: The Security Settings page
3. A dialog box will appear containing information about security and session management changes. Review this information carefully, then click Acknowledge.
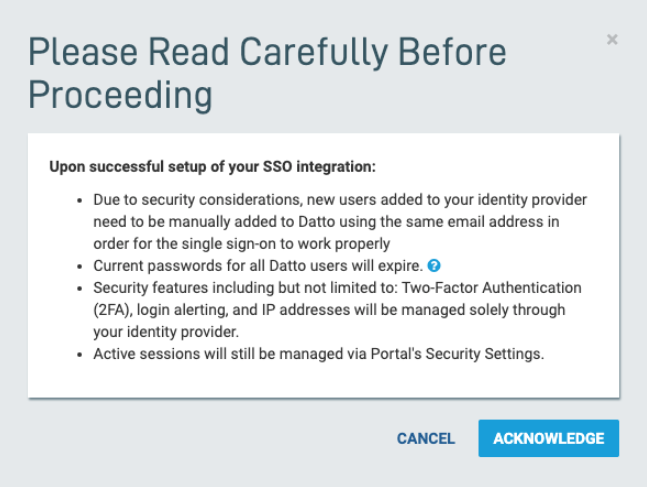
Figure 3: Terms and information
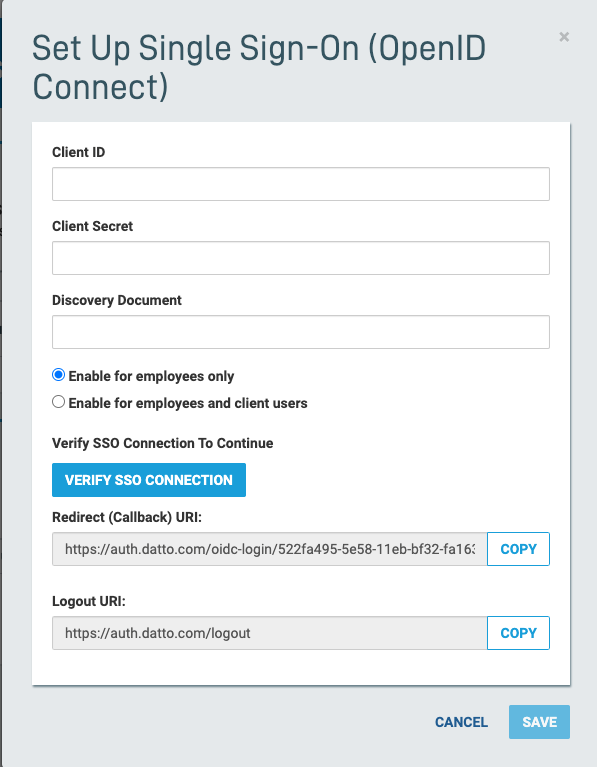
4. The Set Up Portal SINGLE SIGN-ON options will appear. Enter your Organization ID, Organization Secret, and Discovery Document (well-known URL) in the appropriate fields. If this option is enabled, Datto will prefill your email address into your SSO provider as your user name.
5. Copy over the redirect URI and logout URI to set up the Datto one-click SSO icon in your IDP. Datto highly recommends the following IDP configuration settings:
- Scope required for Portal SSO configuration:OpenID, Email
- Required Grant Types: Authorization Code
- Required User Attribute: Email
NOTE Make sure your IDP Discovery Document correctly reflects the IDP environment for SSO as any discrepancy may end up in SSO not working
6. Click Verify SSO Connection to continue.
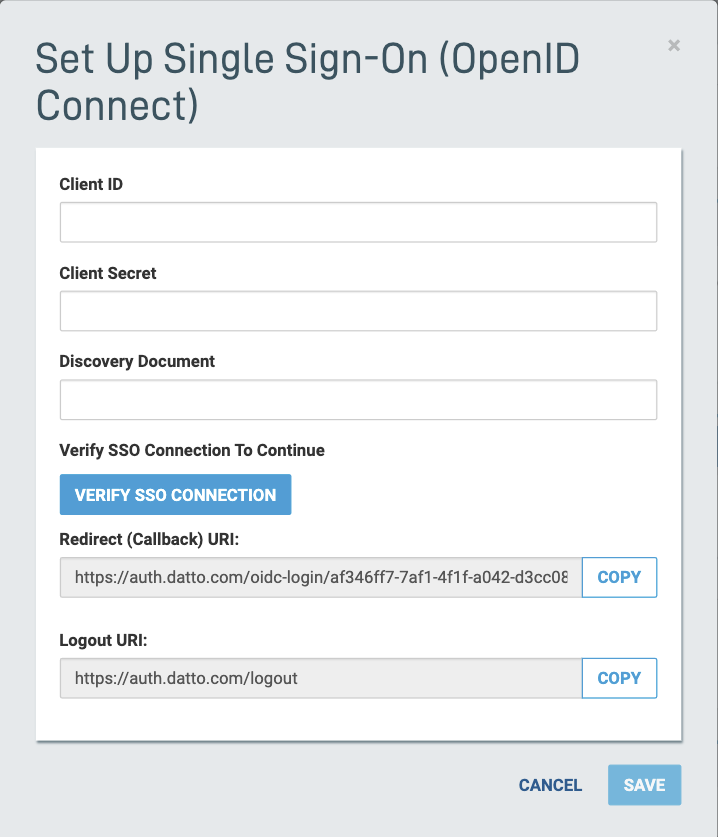
Figure 4: Portal SSO setup options
7. Once the system successfully verifies your SSO connection, click SAVE.
8. Once you complete the setup, you will see a confirmation on the Single Sign-On (SSO) section of the Datto Partner Portal's Security Settings page.
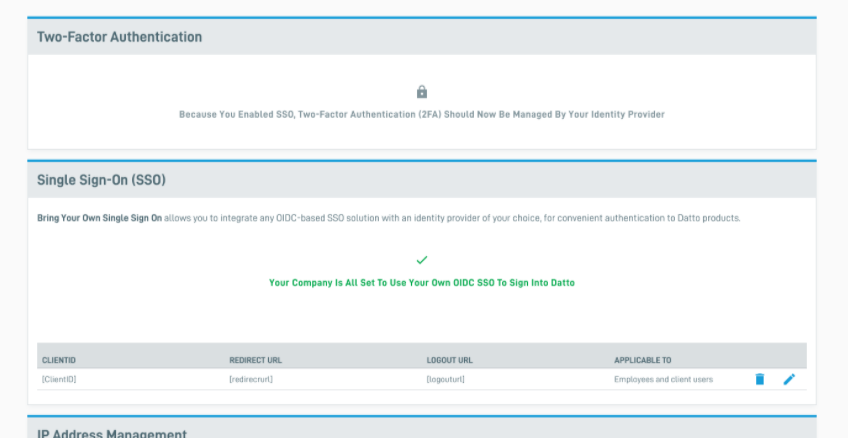
Figure 6: Confirmed setup on the Security Settings page
After setup is complete, all your company's users will only be able to log into Datto through Single Sign-on.
You can modify your SSO information after completing the setup procedure.
1. On the Security Settings page, click the pencil icon next to the account you wish to edit.
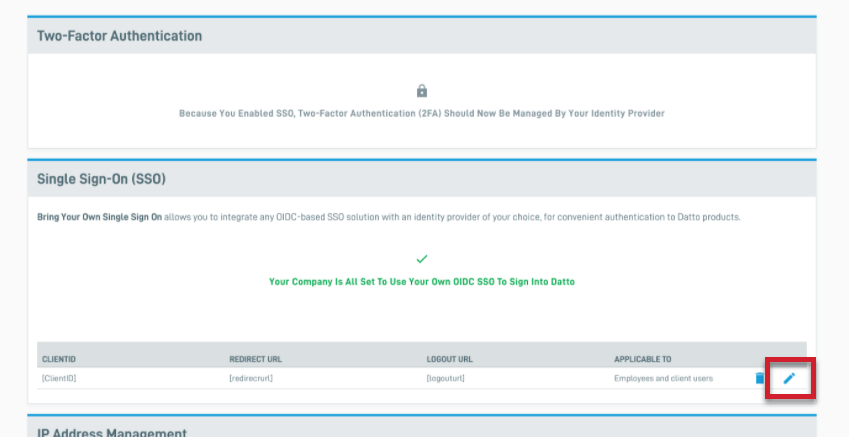
Figure 7: The Edit Your Own Portal SSO icon on the Security Settings page
2. Use the radio buttons to choose whether to enable OIDC SSO for employees only, or for employees and organization users.
Click VERIFY SSO CONNECTION. Once the system successfully verifies your SSO connection, click SAVE.
If you remove your Single Sign-on account, all future logins will be via the Datto username and login.
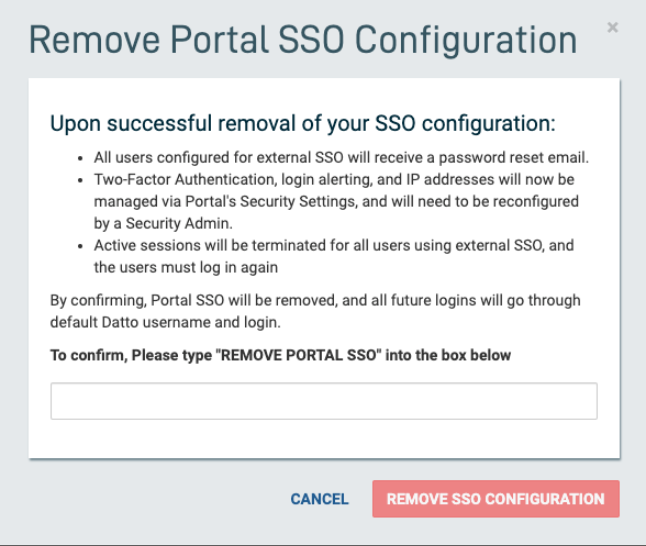
1. On the Security Settings page, click the trashcan icon next to the account you wish to remove.
2. A dialog box will appear. Type "REMOVE PORTAL SSO" into the text field to confirm, then click the REMOVE button.
3. Another dialog box will appear which details the authentication changes that will affect users after you remove your Own Portal SSO. Review this information, then click Acknowledge to complete the removal. All users will receive a password reset email. They must reset their passwords before they can log into Datto again.
Your company's IDP sign-in process
1. The Security Admin will create a Datto icon in the IDP dashboard. Users signing into their IDP should click that icon.
2. The system will redirect the user to Datto with authentication details.
3. The Portal completes the OIDC SSO authentication process and directs the identified user to the Partner Portal homepage/account selection page.
Datto login page sign-in process
1. Users should navigate to the Datto sign-in page and enter their email.
2. The Portal will identify the provided user email and initiate the Portal SSO authentication process with your IDP.
- If the user is already logged into their IDP, that system returns authentication to the Portal.
- If the user is not logged into their IDP, the system redirects the user to the IDP login page. After a successful login, the IDP returns authentication info to the Portal.
3. The Portal completes the Portal SSO authentication process and directs the identified user to the Partner Portal homepage/account selection screen.
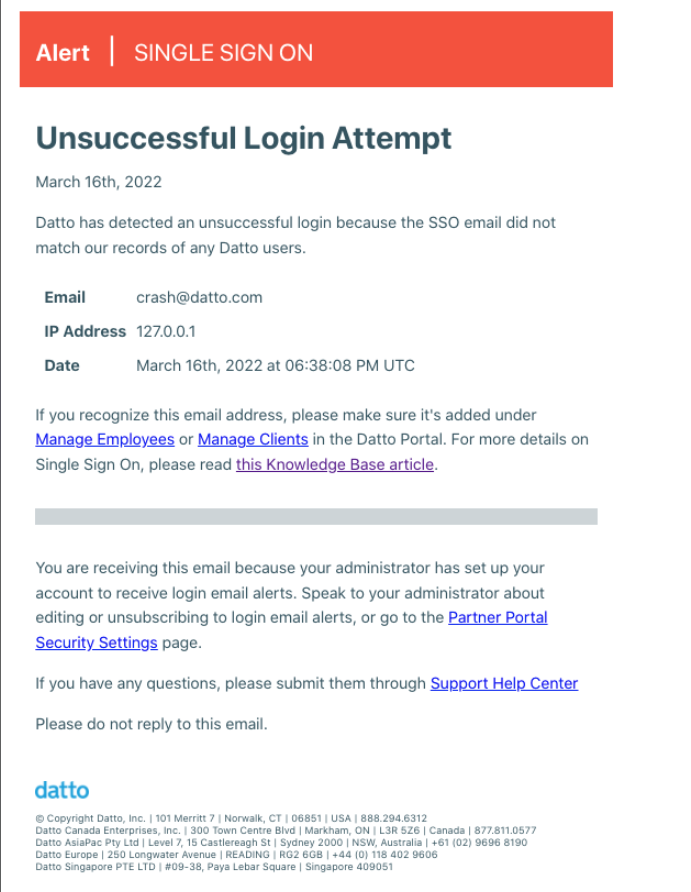
Unsuccessful login alerts
You can configure the Partner Portal to send email alerts to the Security Admin, and other team members you designate, from the Email Alerts card on the Security Settings page.
FAQs
Portal SSO is the capability to seamlessly log into Datto Partner Portal over OpenID Connect protocol, using an off-the-shelf federated single-sign-on solution provided by IDPs (identity providers) like Ping, Okta, Microsoft Entra ID etc.
Using separate credentials to log into Datto and other applications, is inconvenient, insecure and error prone. In addition, the administrators have to manage users in each application including Datto making it redundant, inconsistent and insecure.
Once you start using SSO you won’t require separate credentials and seamlessly and securely login to Datto along with other applications and your security admin can centrally control authentication and deploy consistent security policy.
Portal SSO is based on OIDC, a modern, very secure and lightweight identity protocol specially built for authentication.
By using Portal SSO you can use the state of art security features like multifactor authentication, password, IP & session management, etc. from your identity provider based on your needs. This will enable you to centrally control and consistently deploy security policies across all applications(in use) including Datto.
No, once Portal SSO is configured and enabled, portal authentication security features including MFA, IP management, login alerts will not be available.
No, you can’t use your Datto username and password once Portal SSO is enabled. As soon as you enter your email on the Datto partner portal login page you will be redirected to your SSO IDP for authentication as per configuration.
Portal SSO is designed to be compatible with almost all IDPs like Ping, Okta, Microsoft Entra ID, etc. that support OIDC based single sign-on capability.
As a partner you can only configure one IDP for SSO at any given time but there is no limitation on which IDP you use as long as it supports OIDC protocol for single sign-on.
To configure Portal SSO in portal you need provide below info on the Security Settings page(available to security Admins only):
- Organization ID - Unique application identifier generated by IDP
- Organization Secret - Unique application secret for communication with IDP
- Discovery Document - OIDC based endpoints info
Portal SSO can be configured and used by both Employee as well as Organization users in partner Portal provided all those users are configured under the same identity provider.
No, once you configure Portal SSO in partner portal the users are automatically mapped between your IDP and portal(on the user's first SSO login) but you need to make sure that all users(email) in your IDP have a corresponding account(same email) in the Datto Portal for SSO to work successfully.
Considering the privacy and security of every partner the users belonging to more than one partner will not be able to use Portal SSO and will continue using their existing Datto login credentials.
No, you will need to create a corresponding user account(with the same email) in the Datto partner portal but it will be automatically mapped with the corresponding user account(with the same email) in your IDP on users first SSO login.
Once the user is removed from IDP it will not be able to single sign-on to the Datto partner portal but you will need to remove the corresponding user account(with the same email) in the portal to keep the user accounts in sync.
When Portal SSO configuration is removed/disabled, all related users will receive emails to reset their password and continue login using their Datto login credentials.