Setting up Partner Portal SSO with Azure Active Directory
ENVIRONMENT: Datto Partner Portal
This article describes how to set up Datto Partner Portal SSO (Single sign-on) by using Azure Active Directory.
Datto Partner Portal’s support for external Single Sign-On works by using OpenID Connect (OIDC). This popular, modern protocol is supported by many identity providers, not just Azure Active Directory (Microsoft Entra ID).
If you wish to configure SSO against a provider other than Microsoft Entra ID, you should refer to your OIDC provider’s documentation for how to register an OIDC application, and Datto Partner Portal: Setting up your Portal SSO.
Prerequisites
Before setting up this feature:
- You must have an Azure account with an active subscription.
- The Microsoft Entra ID account you use to configure Datto Partner Portal as an enterprise app should have one of the following roles: Global Administrator, Cloud Application Administrator, Application Administrator.
- This is only required to perform the steps to register Datto’s Partner Portal as an OIDC app, and none of the account’s credentials are used or accessible by the Datto Partner Portal itself.
- Your Datto Partner Portal account must have the role of Security Admin to access the Company Settings page.
NOTE This process requires you to switch between two applications, the Datto Partner Portal and Azure Active Directory. We recommend opening two browser windows, one for each application, to perform these steps.
Key Considerations
- Employee and organization users can only use SSO if the user account email exists in Datto as well as in Microsoft Entra ID.
- Users with an email address associated with multiple reseller Portals cannot use SSO at this time. They can continue using the default Datto (AuthWeb) login process.
- When Portal SSO is enabled, Datto Portal IP Management and Portal Login Email Alerts will be disabled. All authentication security including mfa, IP management, and alerts should be handled by Microsoft Entra ID.
- When Portal SSO is enabled, the system will disregard Datto user passwords and the Change Password feature will not be effective.
- When Portal SSO is configured for Employee Only, users with both Employee and Organization accounts will be unable to use SSO and must log in through Authweb.
- Portal users who have not set up mfa within seven days of account creation will be automatically deactivated. A Portal Admin can reactivate the account and assist with mfa setup to enable Portal login.
How to...
1. Log into the Datto Partner Portal.
2. In the Partner Portal, select the Admin tab, then choose Security Settings from the drop-down menu.
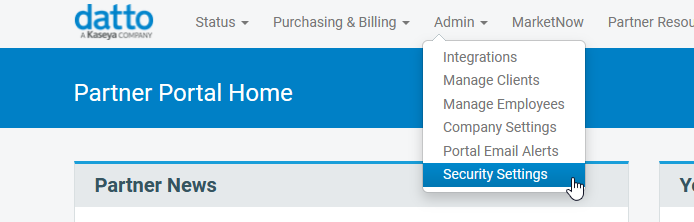
Figure 1: The Datto Partner Portal
3. Click Single Sign-on (SSO).
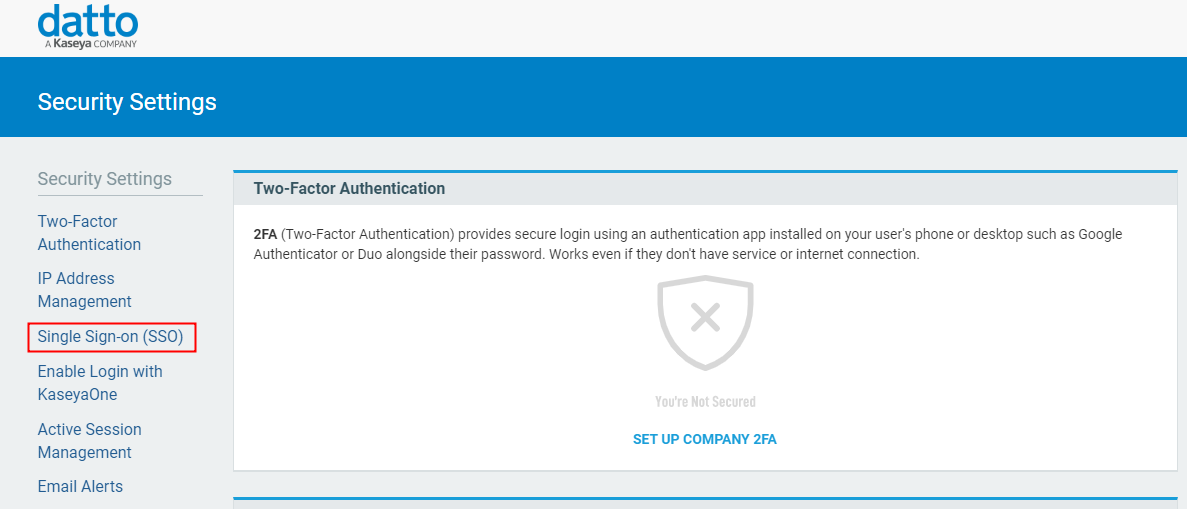
Figure 2: The Security Settings page
4. Click SETUP OIDC SINGLE-SIGN-ON (SSO).
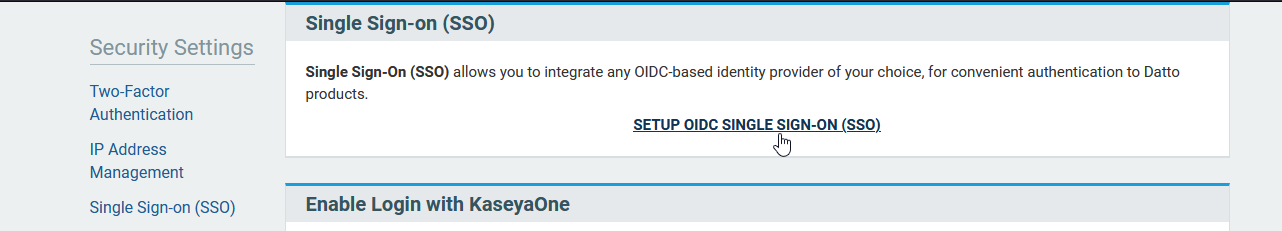
Figure 3: The Single Sign-on card
Read the security information in the pop-up dialog box, then click the Acknowledge button to continue. A second dialog box will open. You will fill in the requested information later in this process.
1. Open a new browser window and log into Azure Active Directory using your primary Microsoft Azure email address. .
2. Navigate to Enterprise Applications and click +New Application.
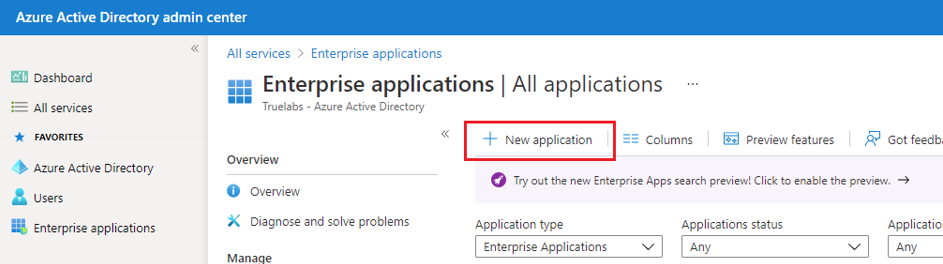
Figure 4: The AAD Admin Center
3. On the Browse Microsoft Entra ID Gallery page, click +Create your own application.
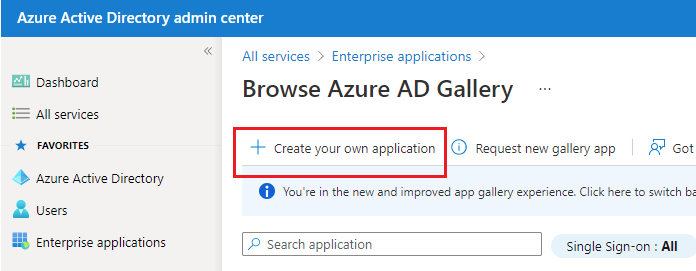
Figure 5: The Microsoft Entra ID Gallery page
4. Enter "Datto Partner Portal" as the name of the app, and select Register an application to integrate with Microsoft Entra ID (App you’re developing). When finished, click Create.
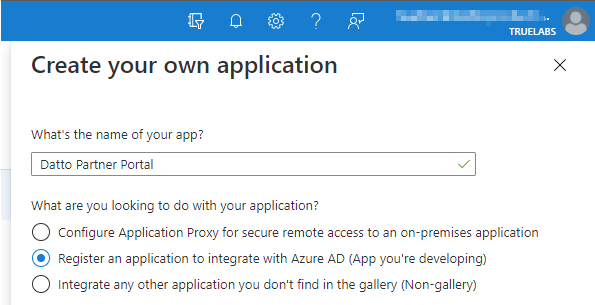
Figure 6: App creation options
5. Return to the browser window you were using to prepare the Partner Portal. Copy the Redirect (Callback) URI.
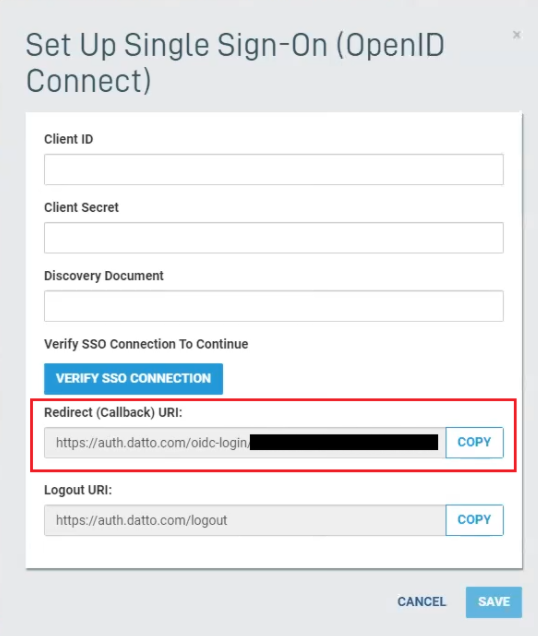
Figure 7: The Redirect (callback) URI in Partner Portal setup
6. On the Redirect URI (optional) page in AAD, paste the URI into the designated field and click the Register button.
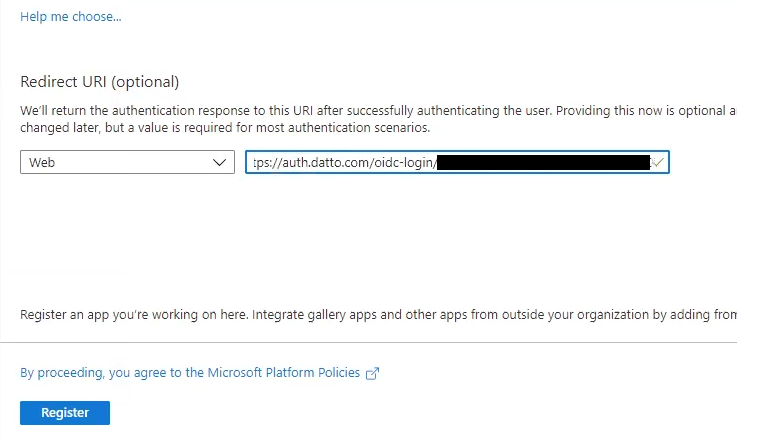
Figure 8: The Redirect URI page in AAD
7. Click Enterprise Applications, then click the Datto Partner Portal app. If it has not yet appeared, wait a few minutes, then refresh the page.
8. Under Manage, click Single sign-on, then click the Datto Partner Portal link.
1. On the AAD's Overview page, copy the Application (organization) ID, then return to the Datto Partner Portal and paste it into the Organization ID field in the setup options dialog box.
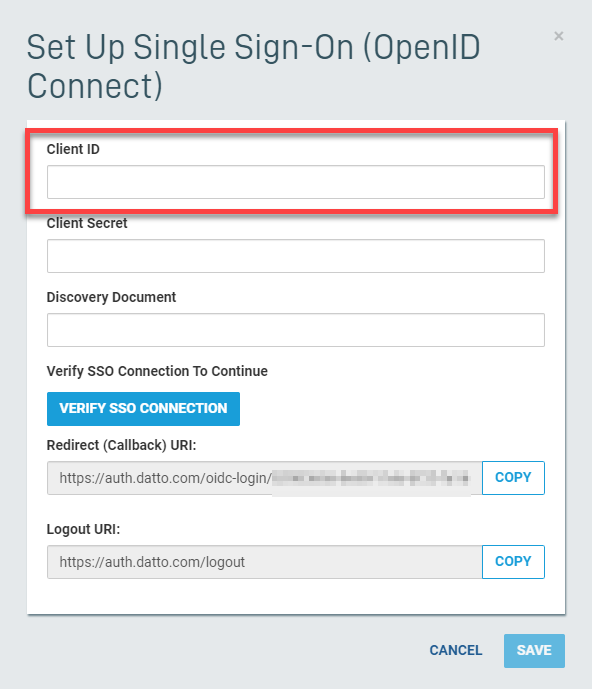
Figure 10: The Organization ID field in SSO setup options
2. Return to the AAD Overview page and click Certificates & secrets.
3. Click +New organization secret.
4. Enter a meaningful description. We recommend "Datto Partner Portal" and the date you created this secret. Then select an Expiry for the Secret that meets your requirements.
NOTE You will need to keep track of the expiration date and renew it prior to that date to avoid loss of access. Datto cannot renew your Organization secret.
5. Under Organization secrets, copy the value (not the Secret ID) field, If you copy the SecretID, the verification step will fail.
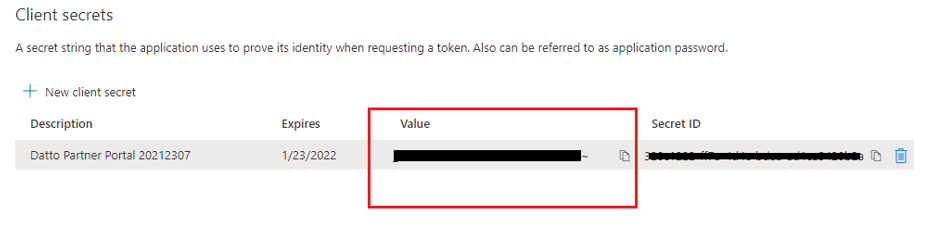
Figure 11: The organization secret value
6. Paste the secret value into the Organization Secret field on the Datto Partner Portal page.
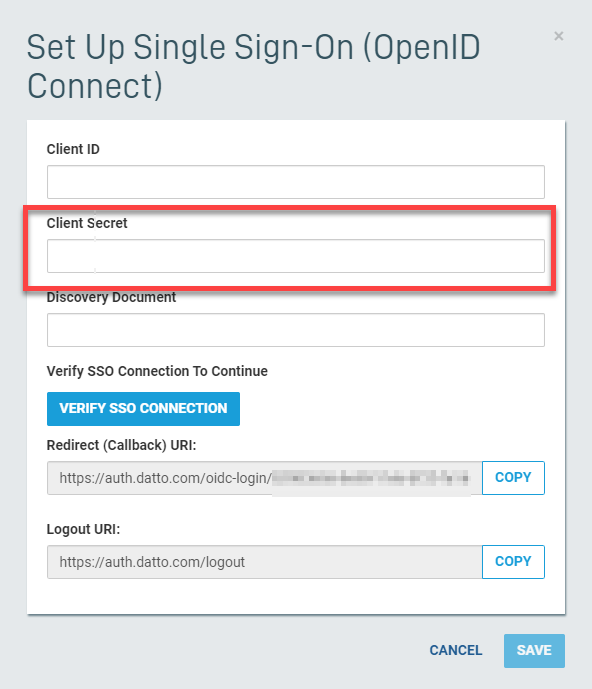
Figure 12: The Organization Secret field in SSO setup options
7. On the AAD page, click Overview, then select Endpoints.
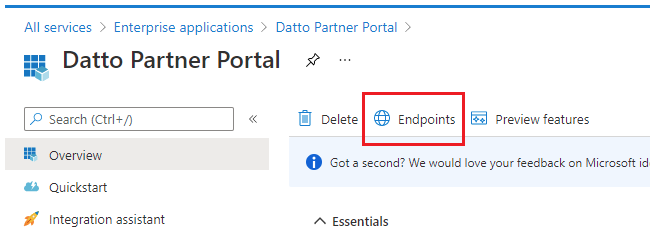
Figure 13: Endpoints on the Overview page
8. On the AAD page, copy the OpenID Connect metadata document, then return to the Partner Portal and paste it into the Discovery Document field, then click the Verify SSO Connection button.
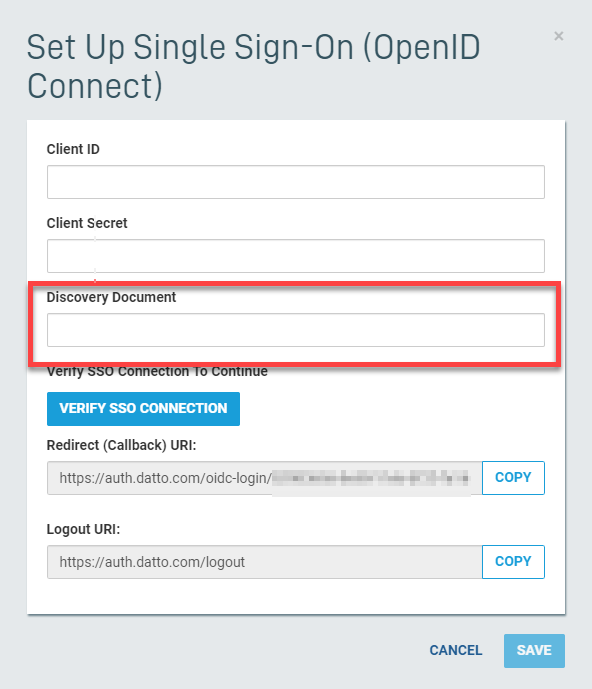
Figure 14: The Discovery Document field in SSO setup options
1. A new tab will open requesting consent from Microsoft Entra ID. This consent authorizes the Datto Partner Portal to know the AAD username and email address of the user when the user accesses the Partner Portal. To understand more about consent, please refer to Microsoft. Check the Consent on behalf of your organization checkbox, then click Accept.
2. If the verification was successful, you should now see a confirmation message on the SSO setup screen. Click Save to complete and save the SSO configuration.
If the verification was not successful, verify that:
- the details are correct
- your Organization Secret is a secret (should appear as a randomized password), and not a GUID or ID.
If the verification process continues to fail, please contact Datto Technical Support.
To verify authentication for yourself, you can try logging in as an authorized user from Microsoft Entra ID from another browser or incognito window, or sign out of the Partner Portal and sign back in again.